How I could delete any video on YouTube | Kamil Hismatullin
About Vulnerability Research Grants
Few months ago Google announced a new experimental program called Vulnerability Research Grants. It's a definitely good idea, thanks Google for inventing and trying such cool things!
How it works: Google's Security team choses regular reporters and send them such emails:
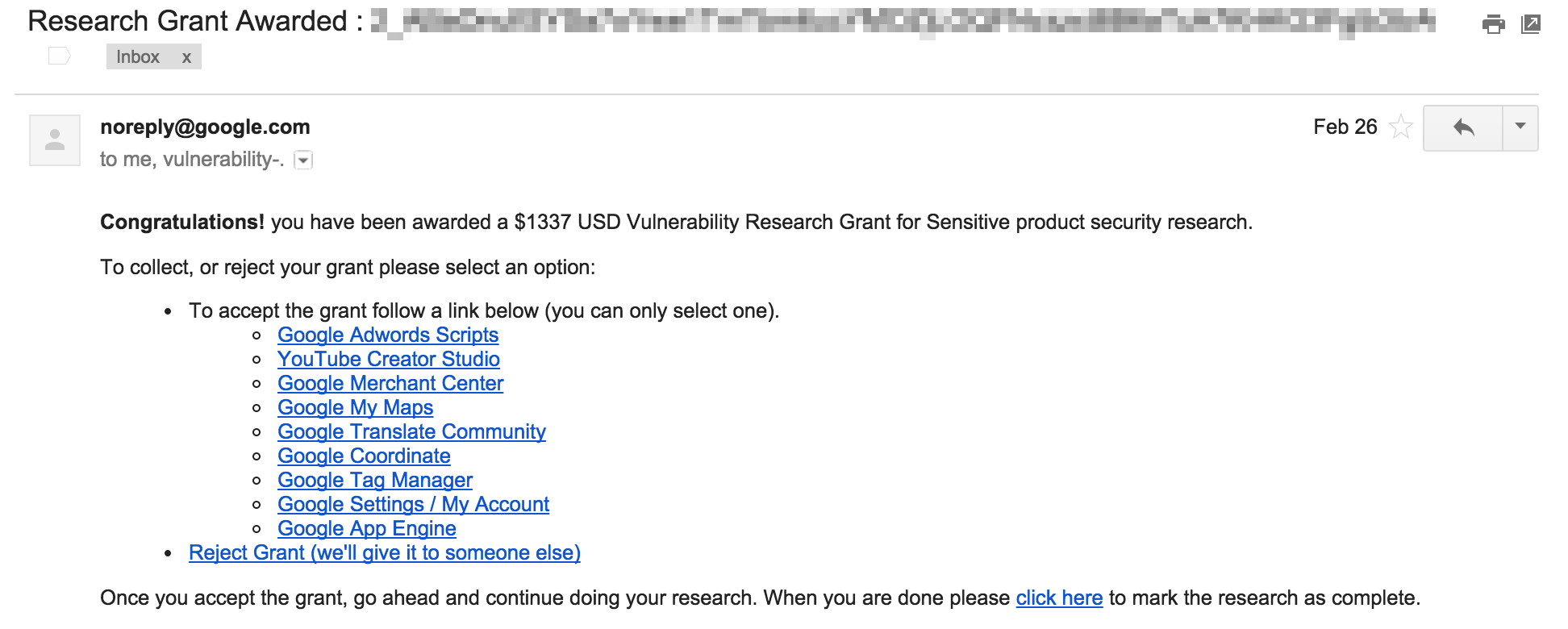
Researcher selects product/service from the list and looks into the security of it. The goal of VRG is to support research looking for vulnerabilities, so even no vulnerability is found, researcher will receive reward for an attention and spent time. But if, as a result of the grant, vulnerabilities are found, then person will receive both reward for detected issues and a grant amount itself.
Security issue on YouTube
As a frequent google reporter, I've received the email above and decided to spend some time on weekends and look into the security of Google products. I selected YouTube Creator Studio as a target and after a few hours I composed two reports. One of them was about easily exploitable, but pretty high severity issue. Here are few words about it.
In YouTube Creator Studio I investigated how live_events/broadcasting systems works. I wanted to find there some CSRF or XSS issues, but unexpectedly discovered a logical bug that let me to delete any video on YouTube with just one following request:
POST https://www.youtube.com/live_events_edit_status_ajax?action_delete_live_event=1
event_id: ANY_VIDEO_ID
session_token: YOUR_TOKEN
In response I got:
{
"success": 1
}
And the video got deleted!
Here is a POC video:
In general I spent 6-7 hours to research, considering that couple of hours I've fought the urge to clean up Bieber's channel haha.
Although it was an early Saturday's morning in SF when I reported issue, Google sec team replied very fast, since this vuln could create utter havoc in a matter of minutes in the bad hands who can used this vulnerability to extort people or simply disrupt YouTube by deleting massive amounts of videos in a very short period of time. It was fixed in several hours, Google rewarded me $5k and luckily no Bieber videos were harmed :D






